CSE641 Cybersecurity for Sustainable Enterprises Report 1
To complete the assessment task, you are required to read the provided case study and write a 750- word report to investigate the applications, security features, benefits and associated security challenges of sustainable and secure enterprise breaches while also exploring the governance protocols and tactics of a resilient and secure enterprise, with emphasis on adherence to existing cybersecurity statutes and regulations.
Please review all the learning resources for Modules 1 to 5 before writing the report. You must also cite at least five (5)scholarly sources(journal articles, book chapters, conference papers) using current Torrens University Australia APA referencing guidelines to support your responses. The sources cited must be included in your reference list.
To complete this assessment task successfully, you must complete the following:
1. Review the Case Study.
• Access the case study from the LMS portal in Module 1.
• Carefully review the case study to understand the specific context and details to formulate your responses.
2. Complete a Case Study Report (750 words).
Based on the provided case study, you will deliberate on the lessons learnt to consider the critical aspects of cybersecurity laws and regulations to sustain and secure enterprises. You will also assess cybersecurity frameworks that comply with the appropriate laws and regulations to prevent cybersecurity breaches.
The report must be written using the following structure.
a) Introduction (approximately 100 words):
i) Briefly introduce the topic of cybersecurity in the context of sustainable and secure enterprises.
ii) Describe the importance for organisations to abide by cybersecurity regulations and adopt governance standards.
b) Case Study (approximately 150 words):
i) Summarise the key details and findings of the case study.
ii) Highlight the breaches or incidents related to cybersecurity in the context of sustainable and secure enterprises.
iii) Assess the impact of these breaches on the affected organisation, including financial, reputational, and operational consequences in the context of sustainable and secure enterprises.
c) Governance strategies and standards (approximately 250 words):
i) Examine the relevant cybersecurity laws and regulations to reduce vulnerabilities and ensure a secure and sustainable organisation.
ii) Explain how confidentiality, data integrity and availability are critical components of enterprise cybersecurity practices.
d) Cybersecurity Compliance Frameworks(approximately 200 words):
i) Discuss the concept of compliance frameworks for sustainable and secure organisations.
ii) Review relevant compliance frameworks applicable to this case study (e.g., NIST, ISO 27001 and the Australian Signals Directorate’s Essential Eight).
iii) Explain how compliance frameworks can help organisations to adhere to cybersecurity regulations and laws.
e) Conclusion (approximately 50 words):
i) Summarise the key findings from the report.
ii) Reiterate the importance of robust cybersecurity policies and procedures for secure and sustainable enterprises.
f) Reference List:
i) Include all sources cited using the current Torrens University Australia APA referencing guidelines.
ii) Make sure at least five (5) references are current, credible and relevant. Using Wikipedia, Investopedia and similar sourcesshould be avoided. This section is not included in the total word count.
3. Use appropriate and professional format, layout and language for your report.
b) Use 1.5 line spacing, a wide left margin, a standard 12-point font (Times New Roman, Calibri or Arial), left-justify body text and include page numbers.
c) Consistently run a spelling and grammar check; however, please remember that such checks may not pick up style, tone and formality errors.
d) Ensure that you edit your work manually and carefully for style, tone and formality.
At current Scenario, organizations have to combat cyber threats to make their organisations sustainable and to secure their enterprise. Cyber security means protecting information, denying unauthorized access and managing risks due to cyber criminals. Robust architectonics protect an entity’s copiousness and credibility (Adel, Sarwar & Hosseinian-Far, 2021).
Implementing cybersecurity regulations and governing security standards is important when dealing with compliance laws like the GDPR and frameworks like ISO 27001. It is thus important for an organisation to tap into its potential and employ effective security measures to avoid acts of malicious individuals. This paper discusses a case on the defective cyber security policies, their consequences, risk management policies and systematic protocols for secure business organizations.
I) Summary
The case focuses on the cybersecurity policies and measures and the best and least efficient practices in the area. These guidelines for MBA Assignment Expert include general password management, handling of data and information, use of internet connection, protection of devices and managing incidents occurring in computer systems. Some of them correlate with the best practice, whereas some of them have vulnerabilities that make organizations prone to cyber threats (Barker, 2023).
For instance, while enforcing that employees should change their passwords often and at the same time type them, you are likely to gain adversaries. Some other risks are forwarding of confidential data on personal devices without encryption and exposure of the devices to third parties without restriction.
II) Incident for Breaches
These flawed policies put this organization at risk of the following cybersecurity threats. Weak passwords give an easy way of obtaining the credentials ,hence access to computers or networks unauthorized persons.
III) Impact
Further, the delay in security reporting on security incidents undermines response measures making attacks progress to new levels. Lack of monitoring and free access to the networks deepens these risks, making enterprise organizations financially and operationally and maintaining its goodwill.
I) Cybersecurity Laws and Regulations
This is mainly because compliance with cybersecurity laws is crucial in lessening the chances of experiencing vulnerabilities in a given firm’s system. Companies must follow the GDPR rules, and due to the CMMC, the necessity to have cybersecurity certifications, as well as data protection regulations (Goyal, 2021). These laws require the use of encryption technology, access control and periodic checks on the data.
There are various industry standards in existence, starting from the ISO 2700,1 to ensure that various risks are effectively managed.
II) Importance of Confidentiality, Integrity, and Availability
The three main components of security are the protection of
1. Data confidentiality: Confidentiality refers to the keeping the sensitive information for away from unauthorised access. .
2. Data integrity: The data integrity refers to the accuracy of data inputs and maintaining proper systems.
3. Data availability: The data availability is a significant fact for accessing the information and systems.
The Confidentiality, integrity and Availability are abbreviated as “CIA” (Unigwe, 2022).
This suggest that information is only shared with the people who are allowed to access it, thereby avoiding loss of such information due to fraudulent activities from within the company. Security helps to prevent alteration of data that would otherwise make it inaccurate or irrelevant. This means a confirmation that information and systems will be reachable as and when required while not being affected by cyber threats.
To support these principles, the organisations should embrace encryption, multi-factor authentication, and security monitoring. Enhancing the system's security and putting measures in place to control access reduces the probability of its exposure and operational interferences.
I) Concept of Compliance Frameworks
Compliance frameworks are regulatory policies that give firms a better structure to achieve these guidelines set to improve a firm’s cybersecurity standing. These frameworks identify measures, policies, or methods to conform to that would contain security measures, risk mitigation approaches, and responses to cyber threats (Folorunso et al, 2024). Compliance is the process of exercising coordination between various departments and holding every organization accountable to limit future losses; hence, a compliance strategy is important for cutting down on risks that accrue from non-compliance as well as fostering organizational continuity. The compliance approach shall be further incorporated to maintain enterprises’ defenses against new threats.
II) Relevant Compliance Frameworks and Their Benefits
There are several cybersecurity compliance standards that assist organisations in dealing with weaknesses and adhering to legal requirements. NIST Cybersecurity is a reference framework that offers five categories: Protect, Detect, Identify, Respond, and Recover.
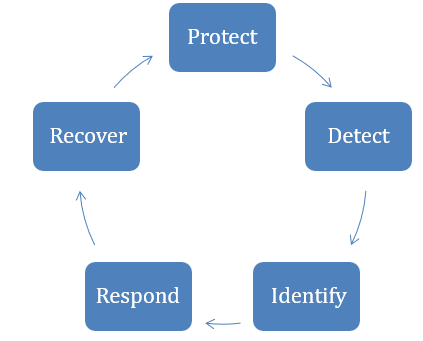
(NIST Cyber Security Framework)
(Made By Author)
Applying these frameworks to the case study’s flawed policies would strengthen the access control, enhance the method in handling incidents, and provide better password protection for enterprises.
III) Implications of applying the cybersecurity laws in Compliance frameworks
ISO 27001 relates to an Information Security Management System that enables to manage risks and protect information assets within an organization (Fonseca-Herrera, Rojas & Florez, 2021).
Applying these frameworks to the case study’s flawed policies would strengthen the access control, enhance the method in handling incidents, and provide better password protection for enterprises.
The case study covers very important mistakes like weak password policies, access control measures, and response to any incident. These weaknesses translate to monetary losses, harm to the public image and limitation of business functioning. By adopting and following such governance strategies together with NIST and ISO 27001, organizations can be guaranteed of a secure performance of their business entities.
Adel, A., Sarwar, D., & Hosseinian-Far, A. (2021, May). Transformation of cybersecurity posture in IT telecommunication: a case study of a telecom operator. In Cybersecurity, Privacy and Freedom Protection in the Connected World: Proceedings of the 13th International Conference on Global Security, Safety and Sustainability,
London, January 2021 (pp. 441-457). Cham: Springer International Publishing. http://nectar.northampton.ac.uk/14354/1/Adel_etal_Springer_2021_Transformation_of_Cy bersecurity_Posture_in_IT_Telecommunication_A_Case_Study_of_a_Telecom_Operator.pdf
Barker, J. (2023). Confident cyber security : The essential insights and how to protect from threats. Kogan Page, Limited. https://ebookcentral.proquest.com/lib/think/detail.action?docID=30723272
Folorunso, A., Wada, I., Samuel, B., & Mohammed, V. (2024). Security compliance and its implication for cybersecurity. World Journal of Advanced Research and Reviews, 24(01), 2105-2121. https://www.researchgate.net/profile/Ifeoluwa-Wada/publication/385525362_Security_compliance_and_its_implication_for_cybersecurity/links/67292516232
6b47637c7aeac/Security-compliance-and-its-implication-for-cybersecurity.pdf
Fonseca-Herrera, O. A., Rojas, A. E., & Florez, H. (2021). A model of an information security management system based on NTC-ISO/IEC 27001 standard. IAENG Int. J. Comput. Sci, 48(2), 213-222. https://www.researchgate.net/profile/Alix-E-Rojas/publication/362062660_A_Model_of_an_Information_Security_Management_System_Based_on_NTC-ISOIEC_27001_Standard/links/62d485bcd351bd24f51fa7c5/A-Model-of-an-Information-Security-Management-System-Based-on-NTC-ISO-IEC-27001-Standard.pdf.
Goyal, A. Understanding Cybersecurity Compliance: Implications and Best Practices for Organizations (2021). https://osf.io/zgp27/download
Unigwe, M. (2022). The views of information security professionals toward information security objectives: confidentiality, integrity, and availability triad. Trident University International. https://search.proquest.com/openview/b733b9e2ccc30abc5e06a4a5f8d3559b/1?pq-origsite=gscholar&cbl=18750&diss=y